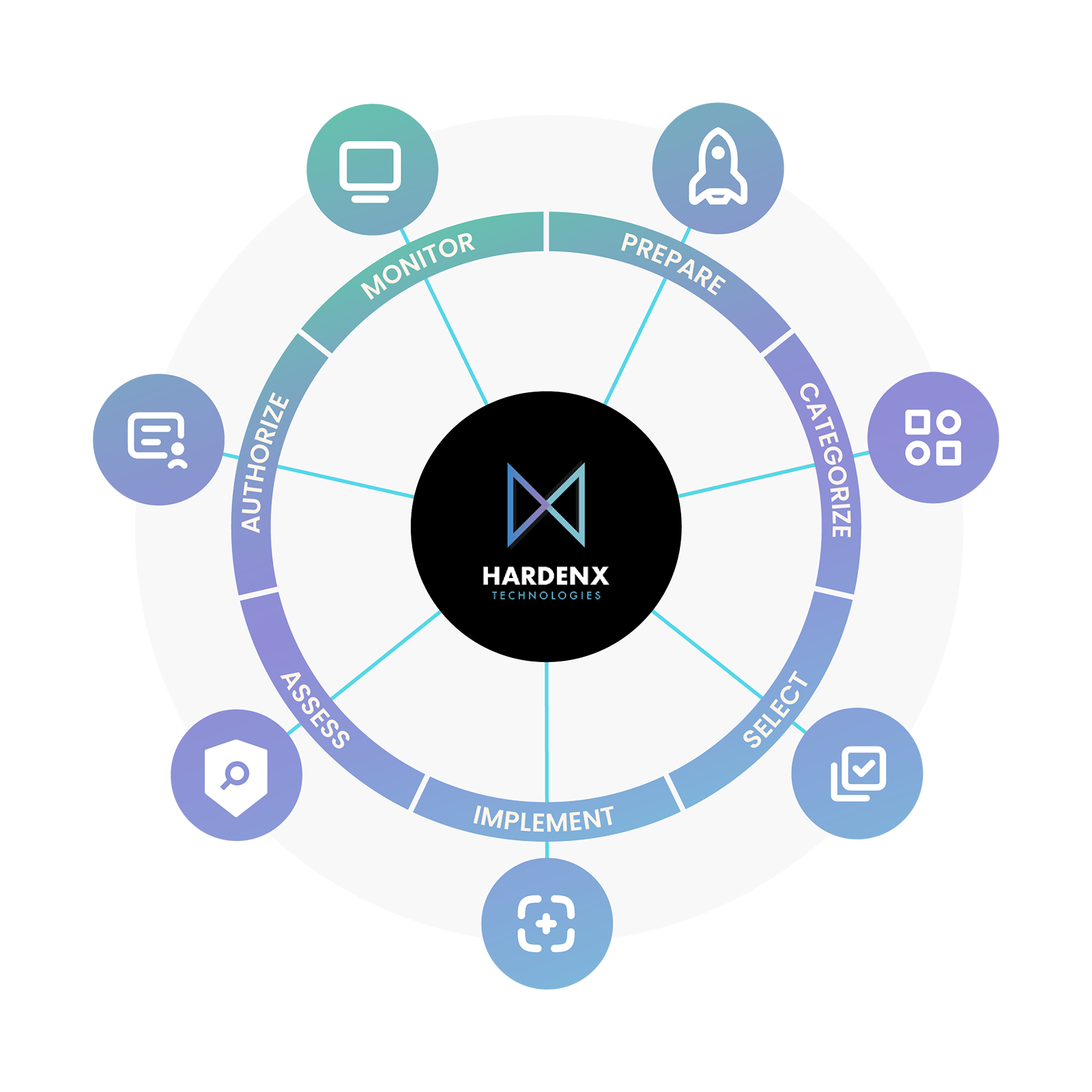
Who We Are
We specialize in system hardening, external risk assessments, compliance audits, and network optimization. Our mission is to secure critical infrastructure, reduce vulnerabilities, and ensure continuous compliance through expert-driven, standards-aligned solutions.